We’ve recently encountered a deceptive scheme circulating that attempts to gain control of unsuspecting individuals’ Upwork accounts. Posing as a “Remote Collaborative” opportunity, this scam is designed to exploit the trust of freelancers and leverage their established profiles for illicit activities.
What the Scam Looks Like:
The scam typically arrives in the form of a document, often titled “Remote Collaborative,” and presents itself as a unique partnership opportunity. The perpetrator, who identifies himself as “Ruslan Danyliuk,” claims to be a professional software developer facing regional IP limitations (specifically, being blocked in Ukraine from accessing Upwork from the United States). To circumvent this, he proposes a “collaborative” arrangement.
Actual image that was sent to us:
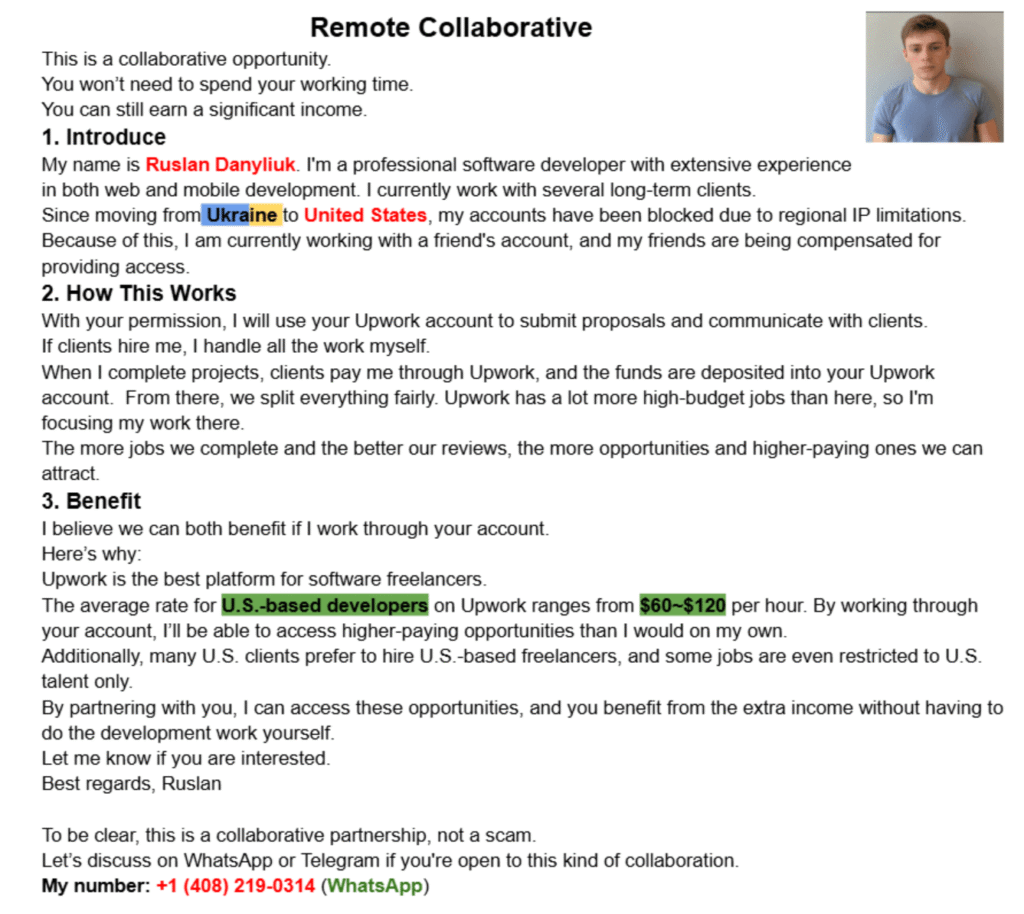
How the Scam Works (and What It Tries to Get You To Do):
The core of this scam revolves around gaining unauthorized access to your Upwork account. Here’s a breakdown of the deceptive steps outlined in the scam document:
- The “Problem” and “Solution”: “Ruslan” claims his accounts have been blocked due to his move from Ukraine to the United States. He then suggests using your Upwork account as a workaround. He states he’s currently working through a friend’s account and that his friends are compensated for providing access – a fabricated detail to normalize the request.
- The “Partnership” Proposal: The scammer proposes that with your “permission,” he will use your Upwork account to submit proposals and communicate with clients. Crucially, he states, “If clients hire me, I handle all the work myself.” This is a critical red flag – the scammer wants to operate as you on the platform.
- The Promise of “Benefit”: To entice you, the scam highlights the supposed benefits. It claims that Upwork is the best platform for software freelancers and that U.S.-based developers (which you presumably are, or he wants to portray you as) command higher rates ($60-$120 per hour). By working through your account, he suggests you’ll gain access to these higher-paying opportunities and additional income without having to do any work yourself. He even claims that U.S. clients prefer to hire U.S.-based freelancers, and some jobs are restricted to them – all designed to make the proposition seem legitimate and advantageous.
The Ultimate Goal of the Scam:
The primary objective of this “Remote Collaborative” scam is to gain complete control over your Upwork account. Once they have access, the scammer can:
- Impersonate you: They will submit proposals and communicate with clients under your name and reputation.
- Engage in fraudulent activities: This could include accepting projects and not delivering, or delivering subpar work, which would damage your professional standing.
- Launder money: Funds from these potentially fraudulent projects would be deposited into your account, only to be “split” with the scammer, effectively using your account as a conduit for illicit funds. This could implicate you in financial crimes.
- Access your personal information: With control of your account, they might be able to access linked payment methods or other sensitive data.
How to Protect Yourself:
- Never share your account credentials: Legitimate collaborations do not require you to give someone access to your personal freelancer account.
- Be wary of promises of easy money: If an offer seems too good to be true (like earning significant income without doing any work), it almost certainly is.
- Verify identities: If someone claims to be a professional but can’t access their own legitimate accounts, it’s a major red flag.
- Report suspicious activity: If you receive a similar proposal, report it immediately to the platform (in this case, Upwork) and block the sender.
- Secure your accounts: Use strong, unique passwords and enable two-factor authentication (2FA) on all your online accounts.
The fact that this scam came as an image instead of plain text is a significant detail and a common tactic used by fraudsters. Here’s why they likely chose an image:
- Evading Text-Based Filters:
- Email Spam Filters: Email providers (like Gmail, Outlook, etc.) use sophisticated algorithms to detect spam, phishing attempts, and known scam patterns. These filters are highly effective at analyzing the text content of emails for keywords (e.g., “opportunity,” “Upwork account,” “money,” “urgent,” “password,” “login”), suspicious links, and common scam phrases. By embedding the entire message as an image, the scammer effectively bypasses many of these text-based filters, making it more likely their message will land in your inbox rather than your spam folder.
- Messaging App Scanners: Similarly, messaging apps (like WhatsApp, Telegram, or even social media platforms) might have automated systems that scan incoming messages for malicious content. An image makes it harder for these systems to “read” and flag the content.
- Preventing Easy Detection and Reporting:
- No Clickable Links: If the scam involved a malicious link, embedding it in an image makes it non-clickable, requiring the user to manually type it, which is less convenient and might make them think twice. (Though in this specific scam, the goal isn’t a link, but account access).
- Difficult to Copy/Paste: It’s much harder for a recipient to quickly copy and paste the scam text into a search engine to verify its legitimacy, or to copy it to report it to a platform or cybersecurity forum. They’d have to manually retype everything, which is a deterrent.
- Hinders Reverse Image Search (for the scammer): While recipients could do a reverse image search to see if the image has been reported as part of a scam (though less likely for text-heavy images), it’s not the primary text-based detection method.
- Preserving Formatting and Appearance:
- Control Over Presentation: An image ensures that the document’s formatting, fonts, and layout are exactly as the scammer intends, regardless of the recipient’s device or email client settings. This can make the document look more “professional” or official.
- Adding an “Official” Look: The inclusion of a photo (like the man’s picture in the top right corner) adds a layer of perceived authenticity, and embedding it within a fixed image format ensures it displays correctly.
In essence, using an image is a deliberate tactic to sneak past automated defenses and make it slightly more inconvenient for the recipient to verify or report the scam, increasing the chances that the message reaches its intended victim unhindered.
This “Remote Collaborative” scam is a clear example of an attempt to compromise a legitimate freelancer’s account for fraudulent purposes. Always exercise extreme caution when approached with such “opportunities” and prioritize the security of your professional online presence.
